THE Jfrog The security research team warned against a malicious package targeting future crypto Mexc Exchange, seeking to steal funds and flee trading references.
The team published a report on April 15 detailing the “CCXt-Mexc-Futures” package, which uses the legitimate cryptocurrency exchange trading library (CCXT) to redirect user trading requests to a malicious server.
The malicious party establishes an area, very similar to that legitimate. In this case, a user can confuse the false Mexc domain for a legitimate area.
Once a victim falls into the trap, attackers can divert all the cryptographic and sensitive information contained in the trading request.
Consequently, attackers can also steal touches and application interface secrets (API). Subsequently, this compromises Crypto trading accounts.
According to the researchers, “the use of obscure techniques and a fake Mexc website also demonstrates the sophistication of this phishing campaign.” The false website is even promoted to Facebook.
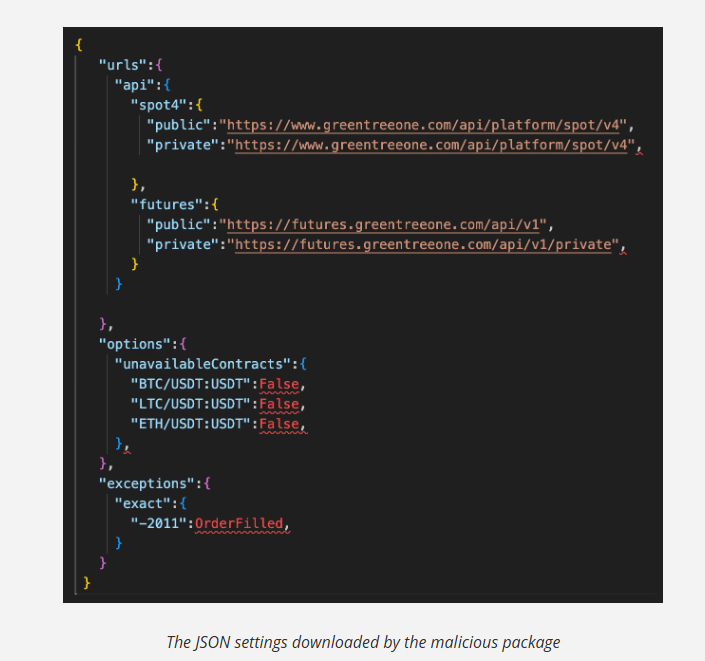
Meanwhile, by entering in more detail, JFROG explains that the CCXT-Mexc-Futures package claims to prolong the crypto trading capabilities via the cryptocurrency (CCXT) exchange trading.
It is a python package with legitimate and popular crypto trading which supports trading on many scholarships, including Mexc.
However, the attackers claim that the malicious package extends the legitimate CCXT package to support the trade of “future” on Mexc.
Instead, to achieve its objectives, the malicious package replaces three relevant functions: describe, sign and prepare_request_headers.
Add, rewrite, redirect, steal cryptographic future
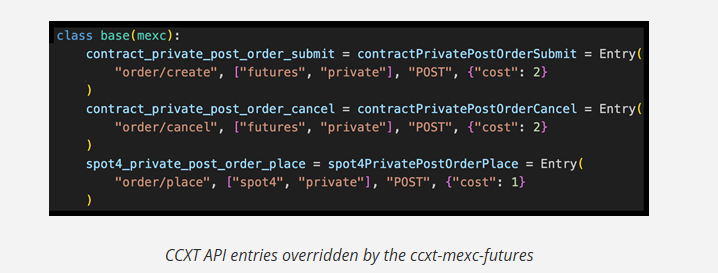
The report continues by explaining that the Mexc interface in CCXT defines a large set of API to support different types of trading. The attackers targeted two of these APIs: contract_private_post_order_submit And contract_private_post_order_cancel.
Once the malicious package CCXT-mexc-futures replaces these two APIs, it adds a third, Spot4_private_post_orde_place.
Consequently, users create, place or cancel trading orders via these APIs which represent the legitimate APIs of the CCXT library.
“Each time a user uses these entries, instead of using the inputs defined by CCXT, he will use the attacker’s entries, specifying trading in the request,” according to the researchers.
In particular, the attackers went even further. They made sure that a “Badrequest” response turns into a “commands” response, so that users think that the order has passed.
In addition, as the malicious package replaces the sign function, if a user tries to communicate with Mexc using the package, requests will go to the false domain.
This also means sending the user token to the attackers’ request.
If the user token is not provided, the package will ask the user to add it before placing a command.
“If this is not an entry linked to the future, the package directs the flow to the original Mexc Exchange implementation of the CCXT package,” notes the report.
Meanwhile, the researchers discovered two versions of the malicious package. They use different methods to hide and run arbitrary code on the victim’s computer who installed the package.
However, the two methods are “very common means for attackers to hide and execute malicious useful loads”.
In response to this threat, Jfrog says that he added the malicious Python packages to Jfrog Xray to allow users to detect them immediately.
The post-New PHISHING diagram targets future crypto on Mexc Exchange appeared first on Cryptonews.





 New security research alert: the JFROG
New security research alert: the JFROG