A new wave of GoBruteforcer botnet malware attacks targets cryptocurrency and blockchain project databases on exposed servers allegedly configured using AI-generated examples.
GoBrutforcer is also known as GoBrut. It is a Golang-based botnet that typically targets exposed FTP, MySQL, PostgreSQL, and phpMyAdmin services.
The malware often relies on compromised Linux servers to scan random public IP addresses and carry out brute force login attacks.

Tackle weak defenses
Check Point researchers estimate that there are more than 50,000 Internet servers that could be vulnerable to GoBrut attacks.
They say the initial compromise is often achieved via FTP servers on servers running XAMPP, because the setup often has a weak default password unless the administrator goes through the security setup.
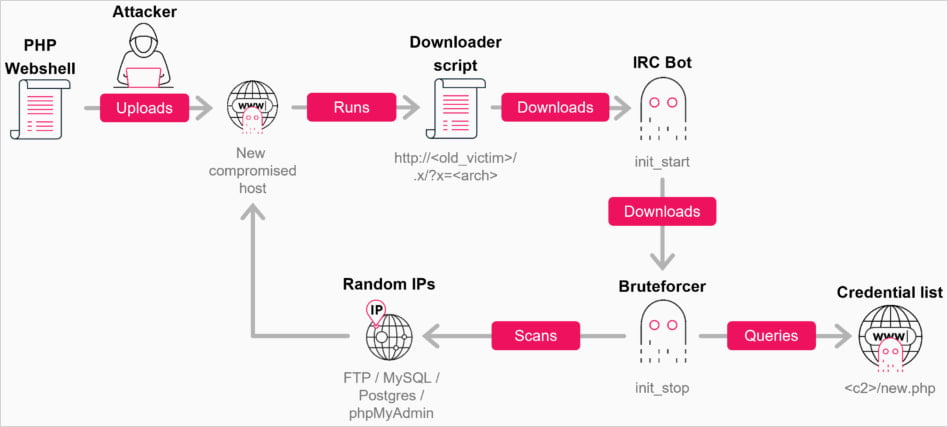
“When attackers gain access to XAMPP FTP using a standard account (usually demon Or person) and a weak default password, the next step is usually to download a web shell into the web root,” Check Point
The attacker can download the web shell through other means, such as a misconfigured MySQL server or a phpMyAdmin panel. The infection chain continues with a downloader, fetching an IRC bot and the bruteforcer module.
Malware activity starts after a delay of 10 to 400 seconds, launching up to 95 brute force threads on x86_64 architectures, scanning random public IP address ranges, while ignoring private networks, AWS cloud ranges, and US government networks.
Each worker generates a single random public IPv4 address, probes the affected service port, goes through the provided list of credentials, and then exits. New workers are constantly generated to maintain the set level of competition.
The FTP module relies on a hard-coded list of 22 username-password pairs embedded directly in the binary. These credentials closely match the default or commonly deployed accounts in web hosting stacks like XAMPP.
Source: Checkpoint
Check Point reports that in recent campaigns, GoBruteforcer activity is fueled by the reuse of common server configuration snippets generated by large language models (LLMs), leading to a proliferation of weak and predictable default usernames, such as application user, myuserAnd operator.
These usernames frequently appear in AI-generated Docker and DevOps instructions, leading researchers to believe that the configurations were added to real-world systems, making them vulnerable to password spraying attacks.
The second trend fueling the botnet’s recent campaign is outdated server stacks like XAMPP that continue to ship with default credentials and open FTP services. These deployments expose vulnerable Webroot directories, allowing attackers to remove web shells.
Check Point’s report highlights a campaign in which a compromised host was infected by TRON wallet scanning tools that perform scans on TRON and Binance Smart Chain (BSC). The attackers used a file containing approximately 23,000 TRON addresses, targeting them with automated utilities to identify and empty wallets with non-zero balances.
Administrators defending against GoBruteforcer should avoid using AI-generated deployment guides and rely on non-default usernames with strong, unique passwords.
It is also recommended to check FTP, phpMyAdmin, MySQL and PostgreSQL for exposed services and replace outdated software stacks like XAMPP with more secure alternatives.

Whether you want to clean up old keys or set guardrails for AI-generated code, this guide helps your team build securely from the start.
Get the cheat sheet and take the guesswork out of managing secrets.




