North Korean pirates have developed fresh and increasingly sophisticated methods to steal cryptography funds: Zoom meetings, hiding malware Github And Npm Packages, and establishing legal entities in the United States, to name only a few.
Recording a real business is the rarest method among these, and it is the most difficult. However, researchers have found several cases of threat actors creating companies in the United States to attract cryptography developers and disseminate a data flight code.
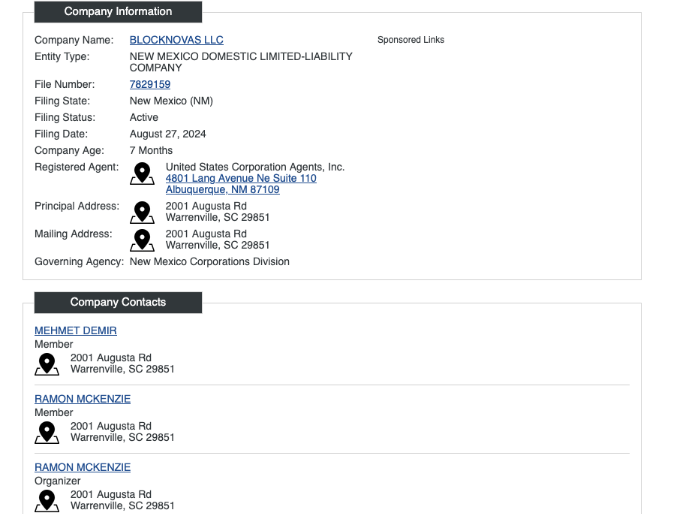
More specifically, according to researchers from the security company SilentThey recorded companies LLC Blocknovas And Softglide LLC In New Mexico and New York, use false identities and addresses. The report shared a list of the false identities linked to the campaign.
The researchers discovered another company, Angloper agencywho has links with this scheme. However, it does not seem to be registered in the United States. Of the three, Blocknovas is the company before the most active, indicates the report.
In particular, Kasey Best, director of information on threats to Silent Push, was cited by Reuters saying that: “This is a rare example of North Korean pirates who have really managed to create legal corporate entities in the United States in order to create business fronts used to attack without distrust candidates.”
In addition, this attack is similar – and can be linked – to the attempted theft of data recently reported by a certain number of initiates in the cryptographic industry.
Nick Bax of Security allianceshared last month that a threat group is trying to steal data and funds through false commercial calls Zoom.
The goal of the attackers is “simple”. Attract crypto developers and infect their devices with malware via a link they send during the interview. They can pretend to encounter technical problems, for example, and will ask the target to click on a link.
Bax said the threat group had stolen “$ 10 from millions of dollars” using this tactic, and others continue to copy it.
Contagious interviews and malicious javascript
Silent Push says what he found is a new campaign. The entity behind it is the North Korean group Apt (Advanced persistent threat) “Contagious interview.‘It is a subgroup of the notorious sponsored by the State Lazarus group.
Better told Reuters that the job interviews “led to deployment of sophisticated malicious software in order to compromise the cryptocurrency portfolios of developers”. In addition, they target passwords and developer identification information, possibly to use it in “other attacks on legitimate companies”.
According to the report, Silent Push confirmed “several victims” of the last interview campaign.
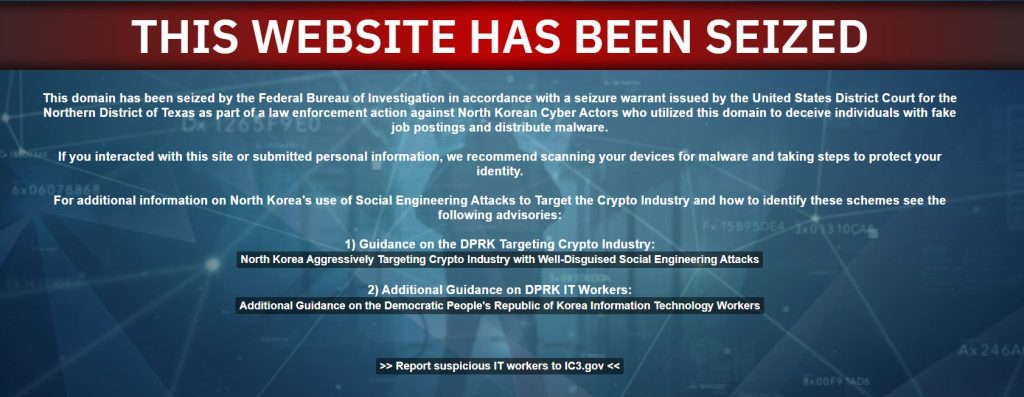
However, the FBI Seized the Blocknovas estate “as part of an action in application of the law against North Korean cyber-actors who used this field to deceive individuals with false job offers and distribute malicious software.”
The other two websites are always operational at the time of writing.
But that’s not all. Another very sophisticated attack line is to insert a malicious javascript in Github NPM standards and packages.
Lazarus started this campaign in August 2024, flying funds and data thanks to supply chain attacks. In addition, this vector of attack evolves.
In particular, malware, called Marstech1, targets crypto-popular portfolios. Various reports have appointed Metamasque,, ExodusAnd Atomic.
Cybersecurity company SecuryCorcard Found 233 victims who installed the Marstech1 implant between September 2024 and January 2025.
The northern post-body is developing new, more sophisticated methods to target the cryptographic industry appeared first on Cryptonews.