Main to remember
- The Lazare group has created false American companies to target developers of the cryptographic industry with Malware.
- The operation represents an evolution of the efforts of North Korea to target the cryptography sector for funding.
Share this article
The Lazarus group of North Korea, through its sub-unit, has shot false companies registered in the United States as part of a campaign for phish Crypto developers and steal their portfolios, according to a new Reuters report.
Companies, Blocknovas LLC and SoftGlide LLC, were recorded in New Mexico and New York using false personalities and addresses. Another entity, Angeloper Agency, would be connected to the operation, but it is not recorded in the United States.
The diagram
Tactics have consisted in creating false companies, establishing a convincing online presence and publishing job lists targeting developers.
The pirates used false identities, invented addresses and real platforms like Linkedin and Upwork to appear legitimate and attract developers. Once the candidates have opted for the candidates, they were taken by false interviews and asked to download test assignments or software.
These files contained malicious software which, once executed, gave attackers access to the victim’s system, allowing them to extract passwords, cryptographic wallet keys and other sensitive data.
The Russian -speaking group used almost identical tactics in the previous campaign
In February, BleepingCompute reported that Crazy Evil, a Russian cybercrime group, had already deployed comparable tactics in a targeted scam against crypto and web job seekers.
A subgroup of Crazy Evil has created a false business called chaunseeker.io, displaying fraudulent announcements on platforms like LinkedIn. The candidates were invited to download a malicious application, Grasscall, which installed malware designed to steal identification information, cryptographic wallets and sensitive files.
The operation was well coordinated, using cloned websites, false profiles and a telegram to distribute malicious software.
The FBI confirms the North Korean link
Kasey Best, intelligence director of threats to Silent Push, said that it was one of the first known cases of North Korean pirates that set up legally recorded companies in the United States to circumvent and obtain credibility.
Silent Push retraced the pirates to the Lazare group and confirmed several victims of the campaign, identifying Blocknovas as the most active of the three leading companies they have discovered.
The FBI seized the Blocknovas Domaine as part of application actions against North Korean cyber-actors who used false job offers to distribute malware.
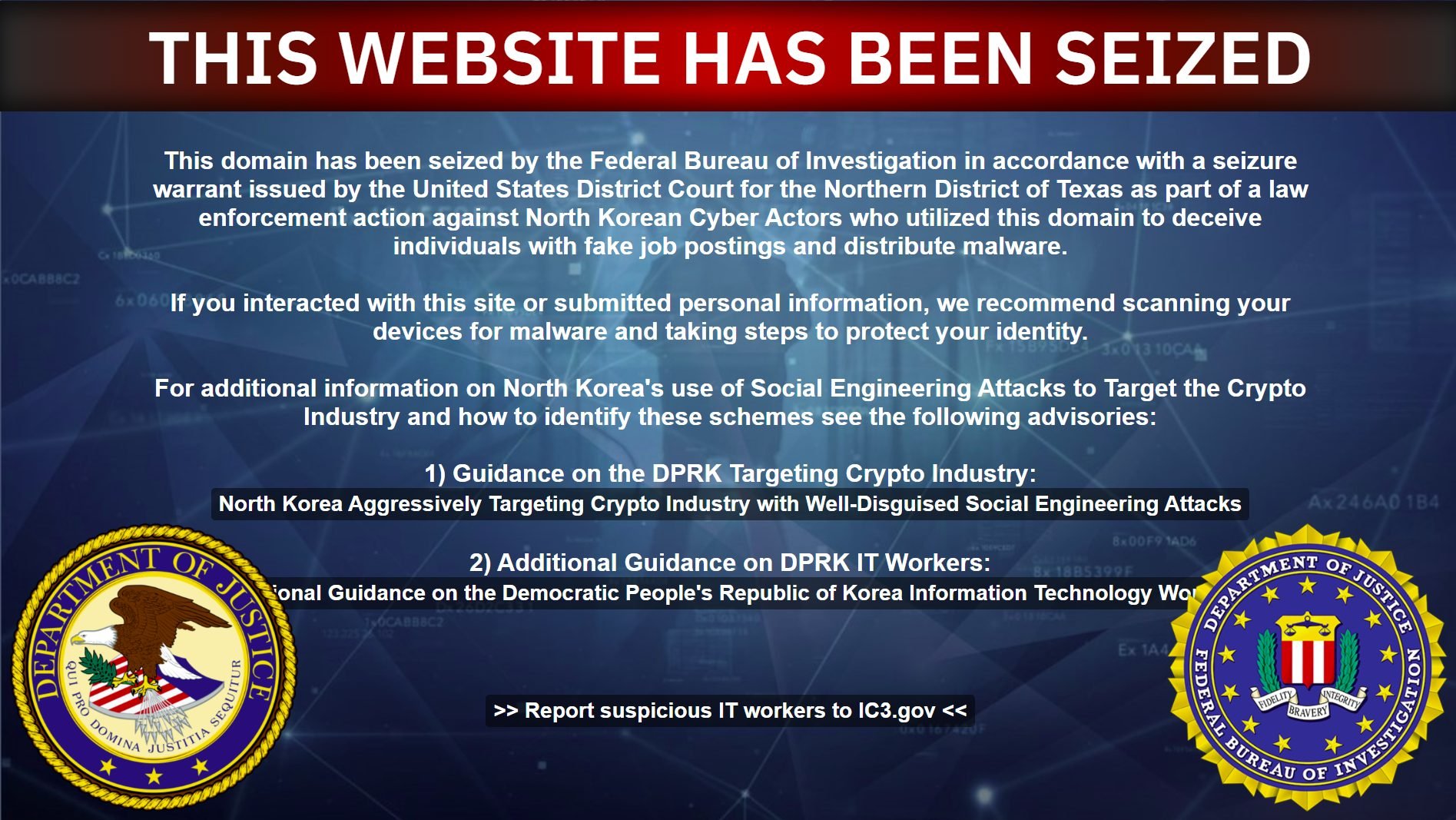

FBI officials said they continue to “focus on the taxation of risks and consequences, not only on the actors of the RPDC themselves, but for anyone facilitating their ability to carry out these diets”.
According to an FBI official, North Korean cyber operations are among the country’s most sophisticated persistent threats.
North Korea exploits the Russian infrastructure on the scale of attacks
To overcome limited national internet access, the North Korea hacking group uses international infrastructure, in particular Russian intellectual property ranges organized in Khasan and Khabarovsk, cities with direct links with North Korea, according to an in -depth analysis of Trend Micro.
The use of VPN, RDP sessions and proxy services like Astrill VPN and CCProxy, Lazarus agents are able to manage attacks, to communicate via Github and Slack, and access to platforms such as Upwork and Telegram.
Silent Push researchers identified seven educational videos recorded by accounts related to Blocknovas as part of the operation. The videos describe how to configure command and control servers, steal browser passwords, download stolen data on Dropbox and break cryptographic wallets with tools such as Hashtopolis.
From the flight to spying sponsored by the State
Hundreds of developers have been targeted, many exposing their sensitive references without knowing it. Some violations seem to have increased beyond the flight, suggesting that Lazarus may have given access to other teams aligned by the State for spying purposes.
US, South Korean and UN officials have confirmed to Reuters that North Korea pirates had deployed thousands of IT workers abroad to generate millions of funds for the Pyongyang nuclear missile program.
Share this article




