
Balancer Protocol announced that hackers had targeted its v2 pools, with losses estimated at over $128 million.
Balancer is a decentralized finance (DeFi) protocol built on the Ethereum blockchain as an automated market maker and liquidity infrastructure layer.
It provides flexible pools with custom token combinations, allowing users to deposit assets, earn fees, and allow traders to trade assets. It is governed by the BAL token, which had a market capitalization of $65 million just before the incident.

Balancer did not share many details about the incident, but warned users to be cautious of possible scams or phishing attempts.
Balancer today confirmed that an exploit affected its V2 Compostable Stable Pools at 7:48 UTC and that the issue does not affect any other Balancer pools, including V3.
“Our team is working with leading security researchers to understand the issue,” the company said in an update a few hours ago.
According to GoPlus Security, the Balancer V2 exploit stemmed from a precision rounding error in the Vault’s swap calculations.
Each swap transaction rounded up the token amounts, creating tiny gaps that the attacker could exploit repeatedly. By chaining together several swaps via the batchSwap function, these rounding losses transformed into a significant price distortion.
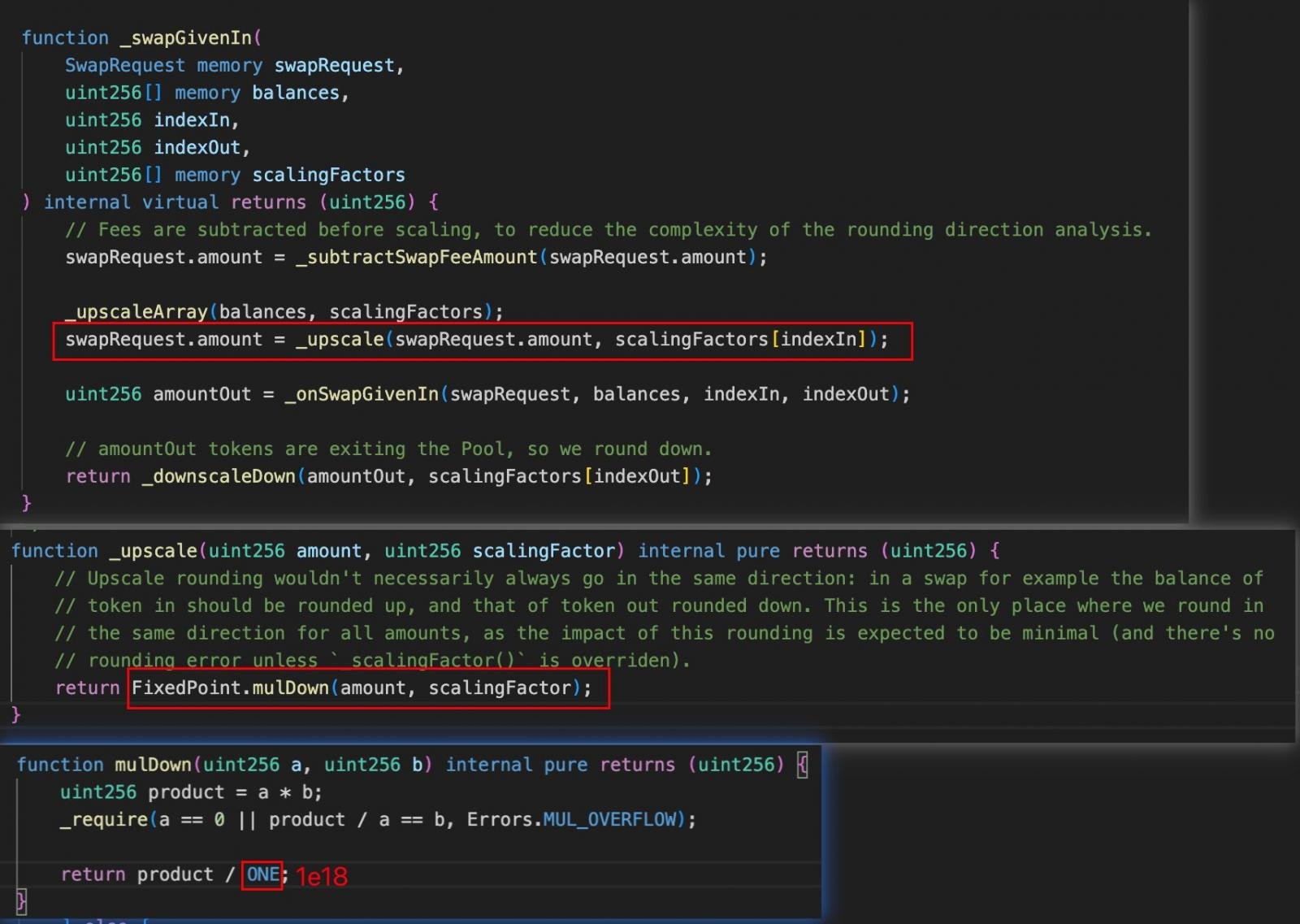
Source: GoPlus Security
However, other users claiming to know what happened attribute the hack to poor management of permissions and recalls in Balancer’s V2 vaults.
According to Aditya Bajaj, a maliciously deployed contract manipulated vault calls during pool initialization, effectively bypassing protections and enabling unauthorized swaps and balance manipulations between interconnected pools.
While there is no agreement yet on the attack method, Balancer promised to share more details about the hack “and a full post-mortem as soon as possible.”
It should be noted that Balancer V2 has been audited 11 times since 2021, with varying scopes of review.
Attempt to deceive the hacker
Meanwhile, it appears someone tried to take advantage of the situation by posing as Balancer and offering the hacker a “white hat bounty” of 20% of the stolen amount if they agreed to return the rest of the funds to a specific address.
The phishing message is well-written and checks tricks to appear credible, including reward, a deadline, and a threat, all within the framework of a negotiation requiring immediate cooperation.
If the hacker refuses the deal, the fraudster posing as Balancer threatens to use whatever information they have from blockchain forensics experts, law enforcement agencies, and regulatory partners to identify and prosecute the attacker.
“Our partners have a high degree of confidence that you will be identified from access log metadata collected by our infrastructure, showing connections from a defined set of IP/ASN addresses and associated entry timestamps that correlate with on-chain transaction activity,” the fraudulent message concludes.
The Balancer hack is one of the biggest cryptocurrency heists in 2025. Although there is no attribution, the biggest threat to DeFi entities are North Korean hackers.
As of October 3, the amount of cryptocurrency linked to North Korean thefts this year exceeded $2 billion, with the largest by far being the Bybit attack in February, where they stole $1.5 billion in cryptocurrency.

Whether you want to clean up old keys or set guardrails for AI-generated code, this guide helps your team build securely from the start.
Get the cheat sheet and take the guesswork out of managing secrets.




